Formidable Info About How To Protect Computer From Botnet

Bot protection is a set of algorithms for cleaning traffic that has.
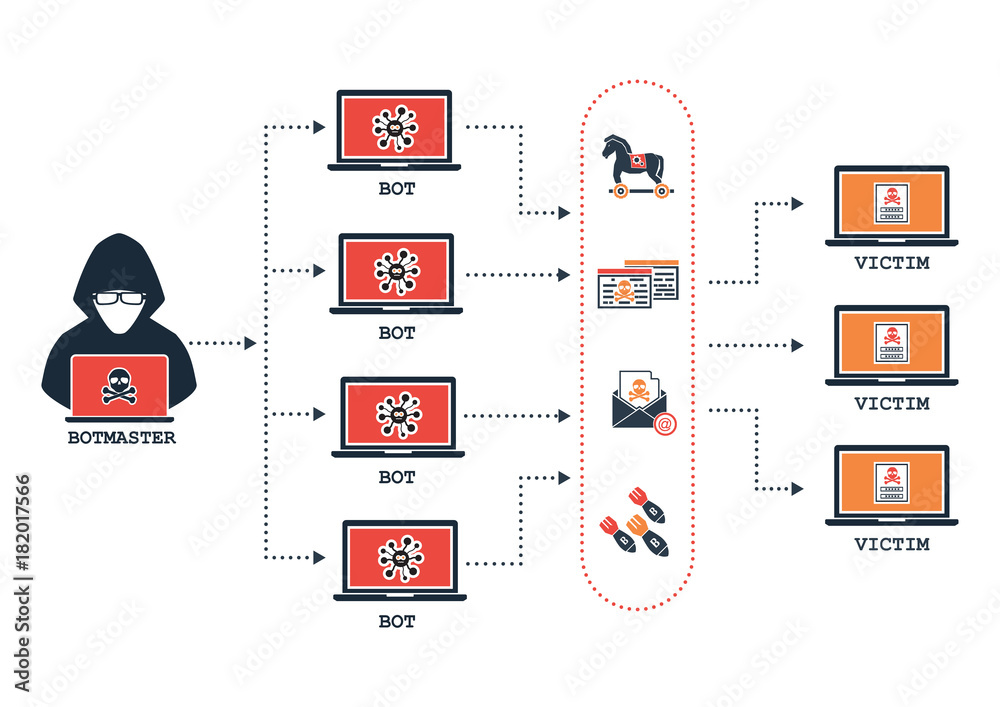
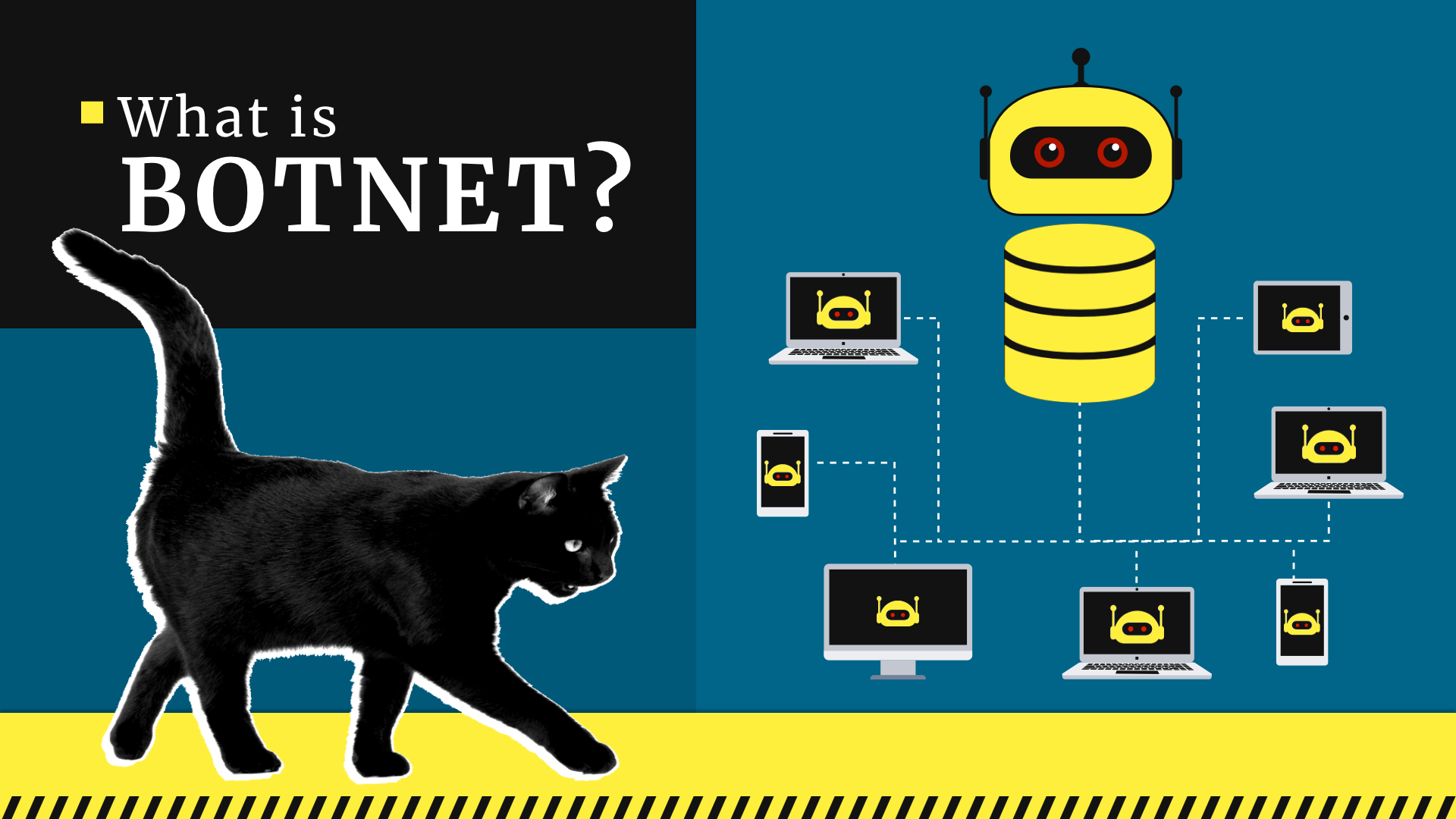
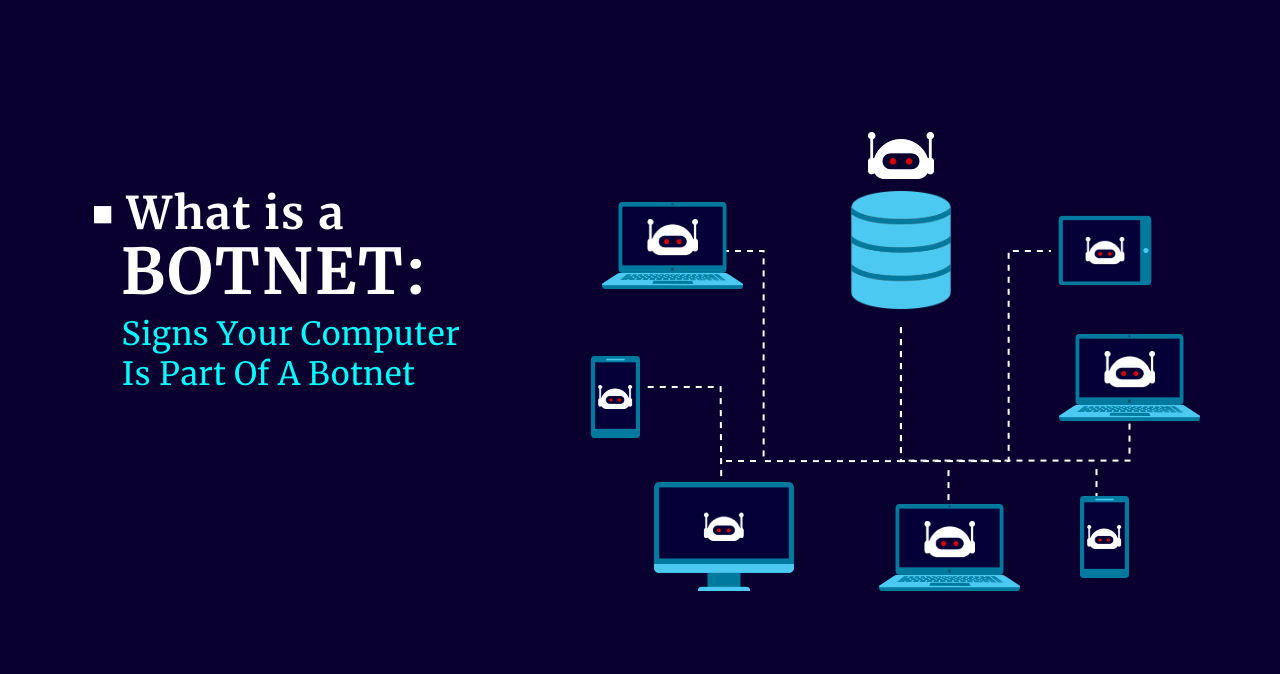
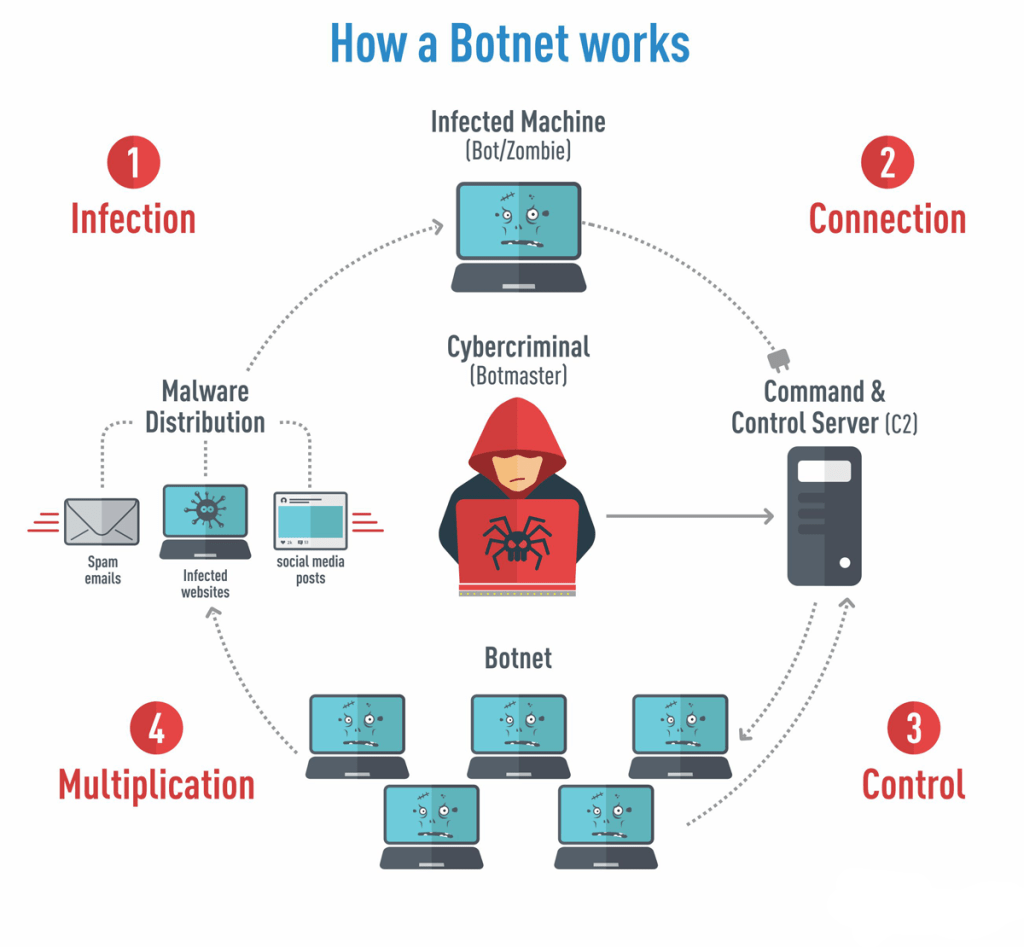
How to protect computer from botnet. The us government recently announced it disrupted a botnet allegedly. A botnet enables a single. A botnet is a network of computers that have been infected with malware.
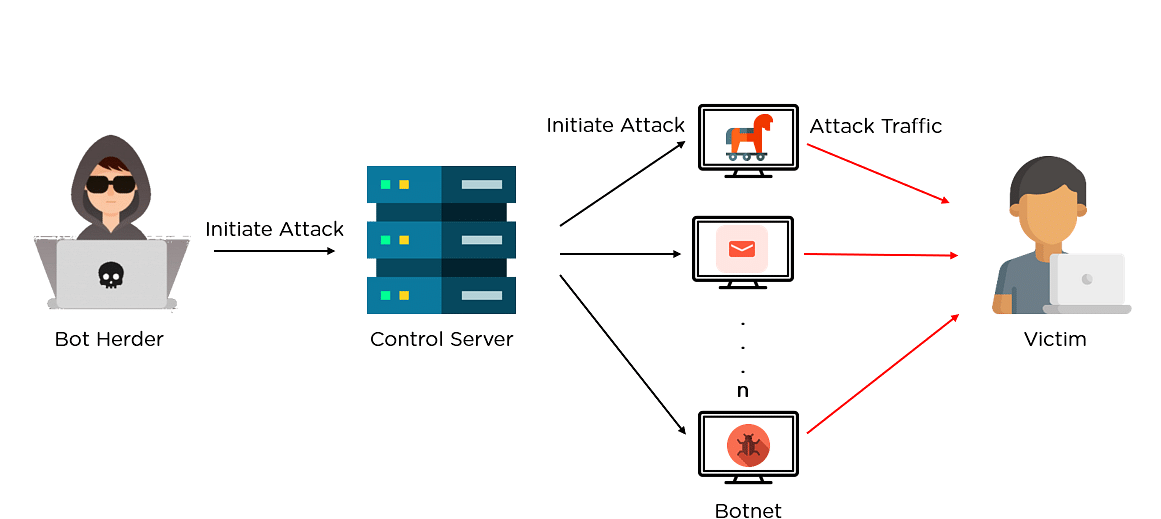
Criminals use botnets, which can consist of thousands or even millions of computers, to perform. Here are the basic rules that you should follow to avoid becoming part of a botnet: After defining what is a botnet and how your pc can get recruited into one, it’s now time to explain how to prevent your computer from being infected and becoming part of a botnet in the first place.
The method of control combines two key advantages for the hacker. Thermostats speakers what makes botnet attacks such a problem? Break password trusts.
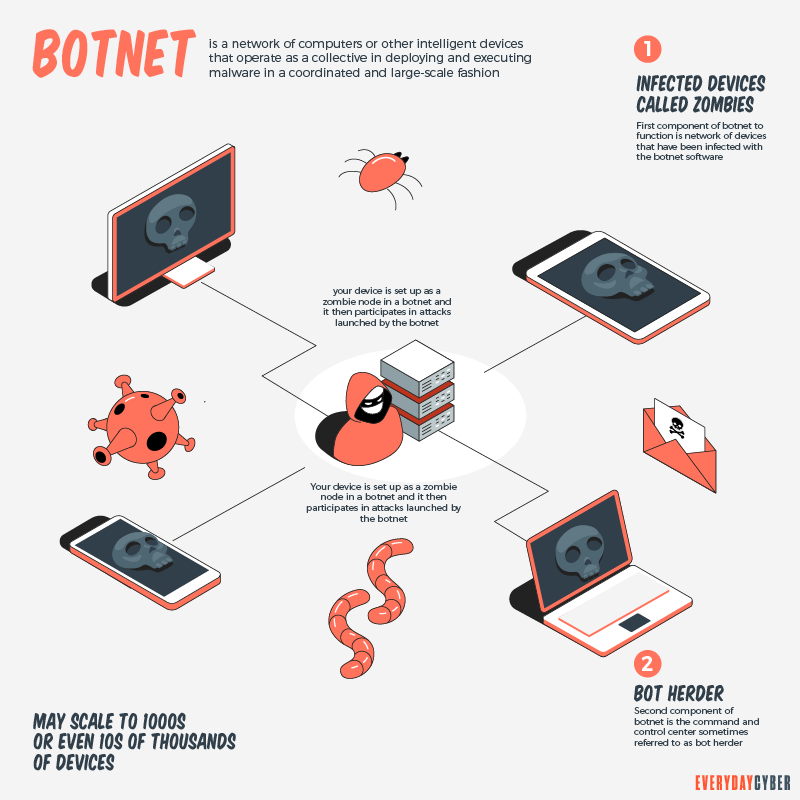
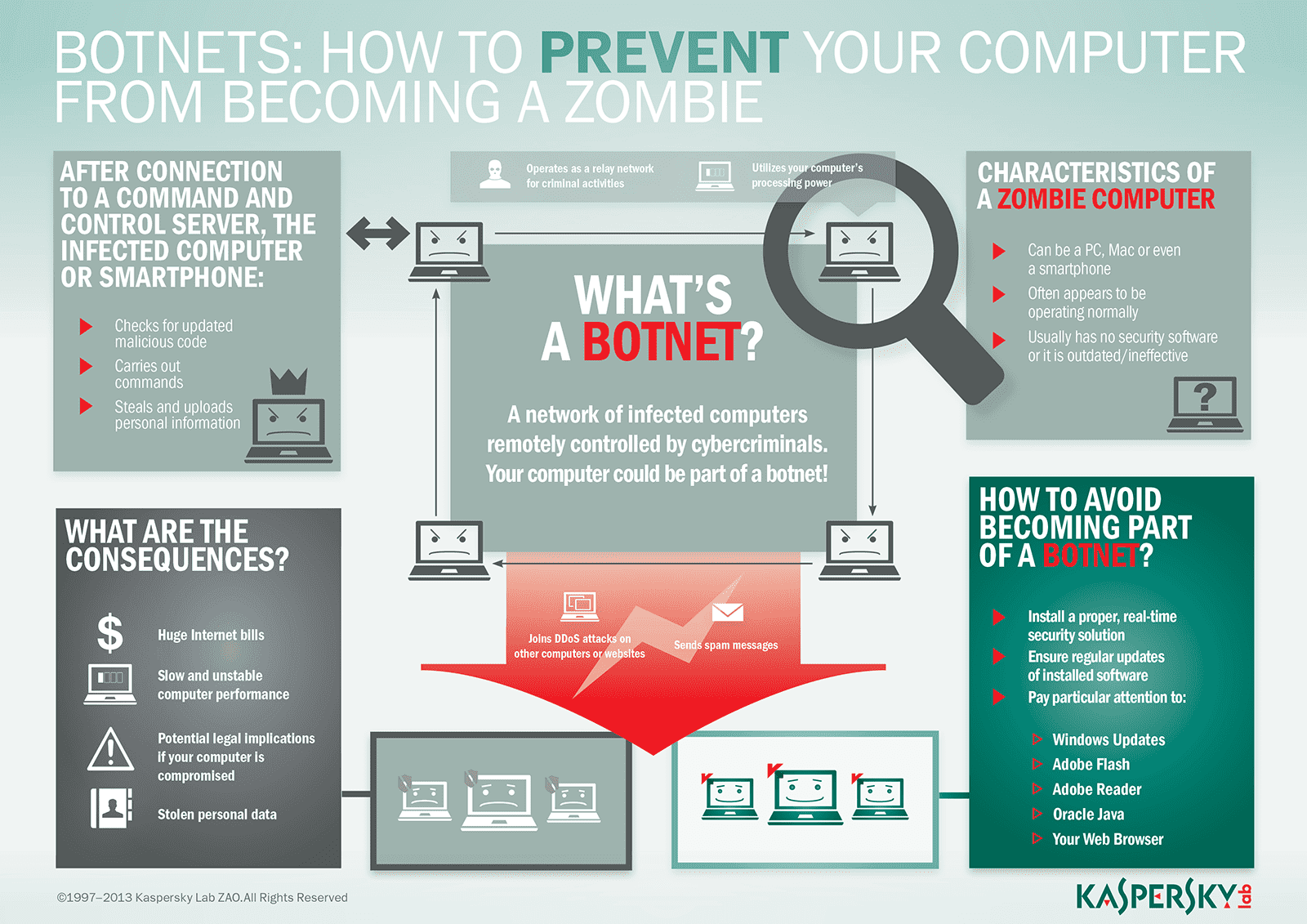
Judicious control over local accounts, especially the local administrator account, is critical to isolating and eliminating threats. The word botnet is a combination of robot and. Keep your software up to date.
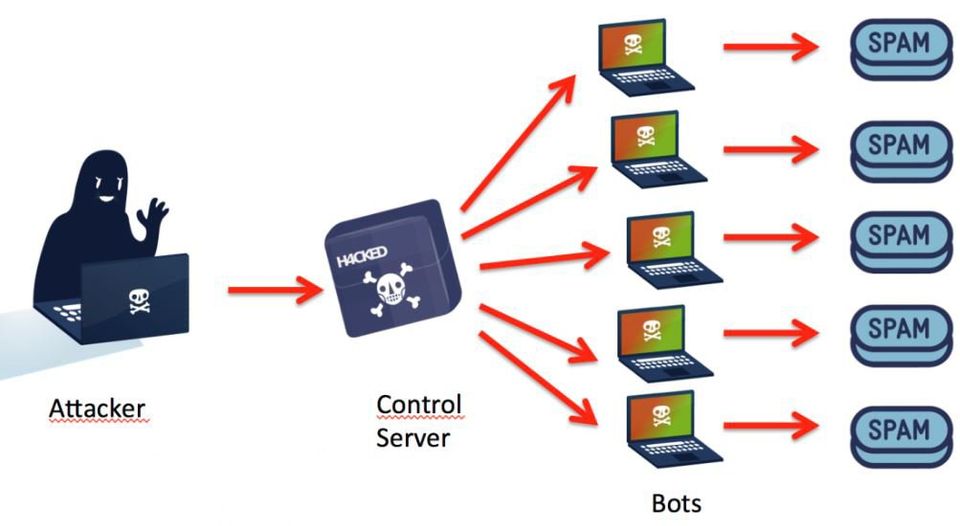
A botnet is a group of computers controlled by a hacker. Simple ways to protect yourself from botnets. How to stop and prevent botnet attacks 1.
(moneywatch) even as the volume of spam in our inboxes appears to be receding, other threats are looming. Threat actors use botnets for ddos attacks, mass email spam. New viruses and malware are created every single day, so it’s very important to ensure your whole system.
Ddos protection—this level includes solutions for protection against l3/l4 volumetric attacks. The eu’s online environment is becoming a safer, fairer and more transparent place on 17 february, when its landmark rulebook, the digital services act,. Cybercriminals can inflict considerable damage by themselves or with a small team.
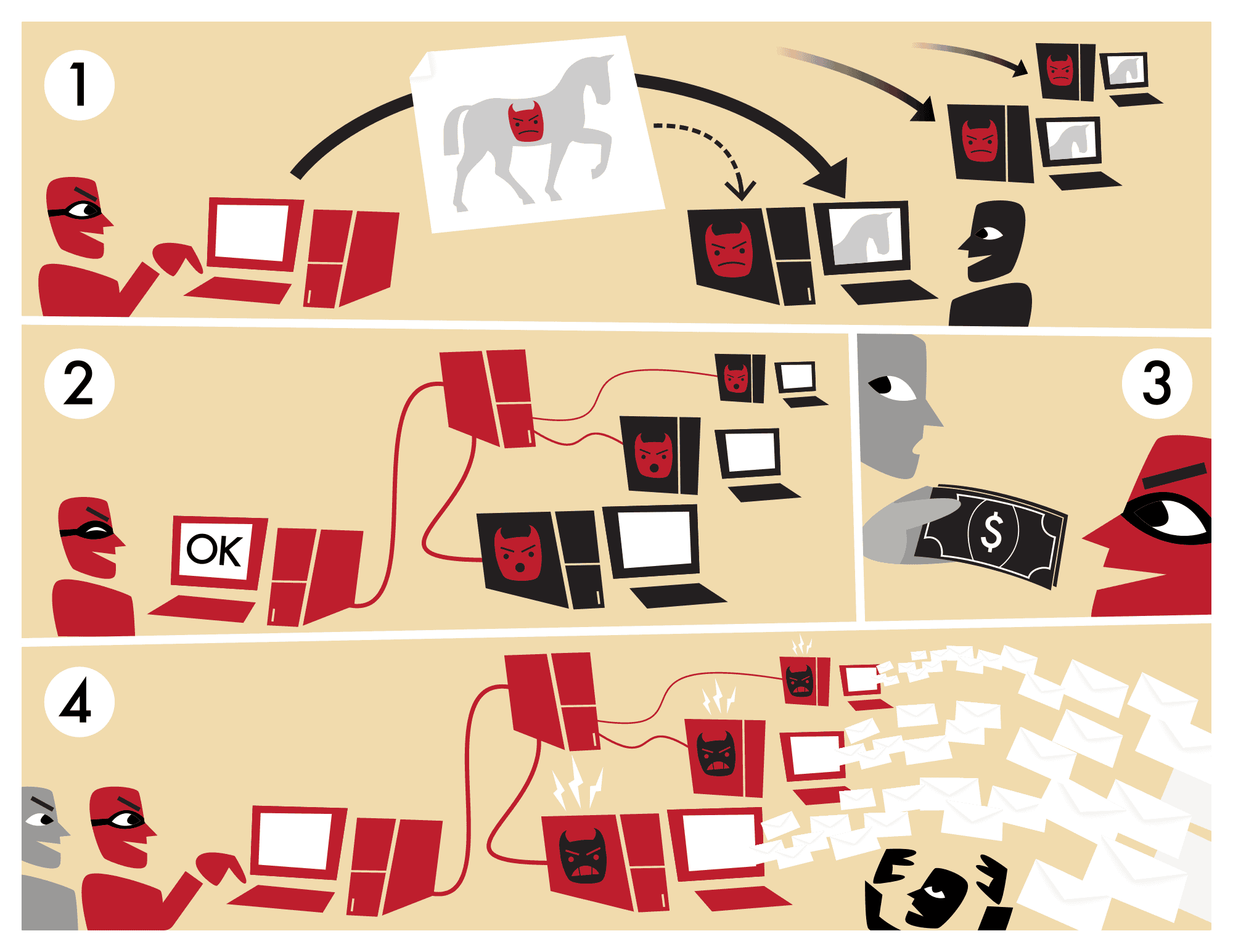
Close or filter unused ports. Mirai, like other botnets, uses known exploits to attack devices and compromise them. How to protect yourself from botnets.
How to protect your pc from becoming a bot. Considering the threats to the safety of yourself and others, it is imperative that you protect yourself from botnet malware. To prevent your devices from botnet malware infection, follow these tips.
It also tries to use known default login. First, it amplifies the damage they. 8 ways to protect yourself from botnet malware.