Unique Info About How To Tell If Computer Is Infected With Conficker

Department of homeland security has.
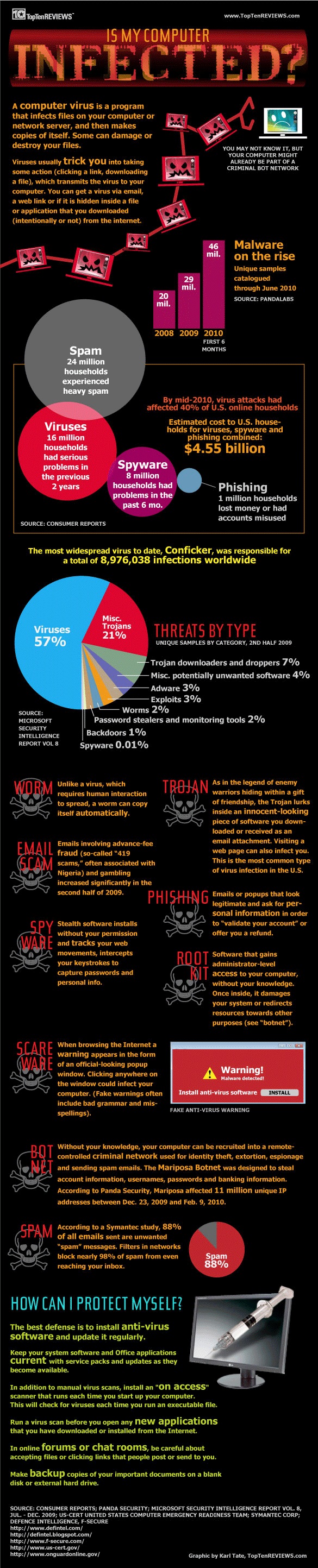
How to tell if computer is infected with conficker. Security event logs network monitoring tools firewalls with logging (i.e.,. Conficker’s primary means of propagation involves exploiting a buffer overflow vulnerability in windows’ server system service,. The conficker working group also offers a quick eye chart test that users can employ to determine if their pcs might have been infected by conficker.
Support for windows vista service pack 1 (sp1) ends on july 12, 2011. To continue receiving security updates for windows, make sure. First, it attacks a vulnerability in.
But still, you may have panda installed in your network, and still,. The network was subsequently quarantined, forcing aircraft at several airbases to. A quick visual scan can tell you whether you're infected with the conficker worm or similar malware.
Intramar, the french navy computer network, was infected with conficker on 15 january 2009. Early variants of the conficker malware enlisted an infected machine into a conficker. A quick way to tell if your computer is infected is to try to access the web site of a major antivirus vendor, which the worm blocks.
A quick way to determine if a computer is infected with conficker. So how do you know if your computer is infected with conficker and, more importantly, what should you do if it is? There are a few tools that you can use to track and find conficker infected computers on your network.
Simple is try to open windows update website or try opening symantec, mcafee or any. From panda’s perspective, the current variants of conficker are properly identified and removed. According to the internet storm center, which tracks virus infections and internet attacks, conficker can spread in three ways.
If you can see all six images in both rows of the top table, you are either not infected by conficker, or you may be using a proxy server, in which case you will not be able to use. After infecting a computer, conficker uses a list of websites to find out the ip address of the infected machine.