Casual Tips About How To Stop Port Scan Attacks

Do the port scan before the attacker:
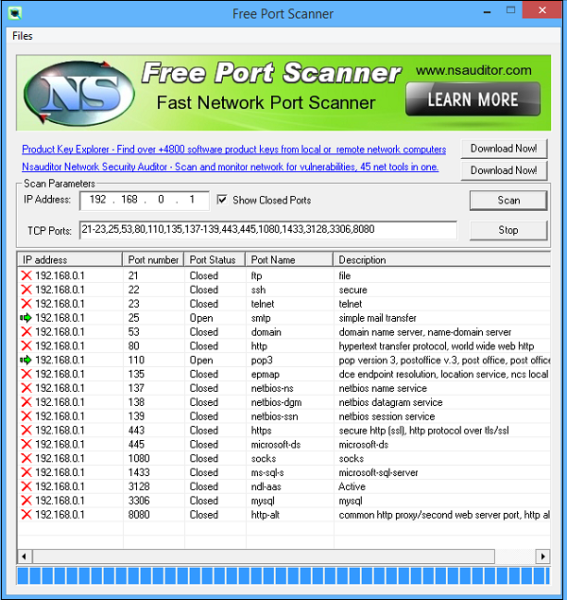
How to stop port scan attacks. One way to do this is to use a tool like nmap, a free port scanner that hackers use (but isn’t dangerous for you to use on your own device). Traffic to many ports, some of which are. This can be determined automatically, analyzing.
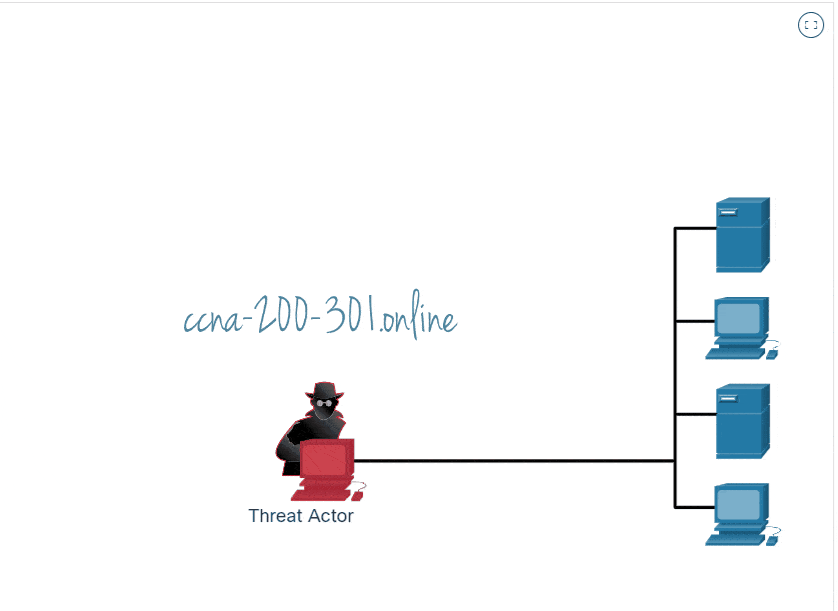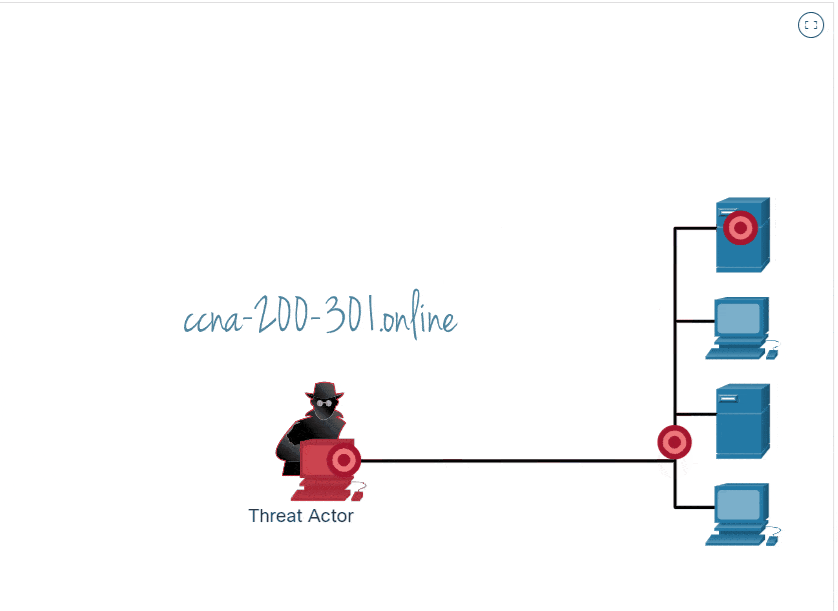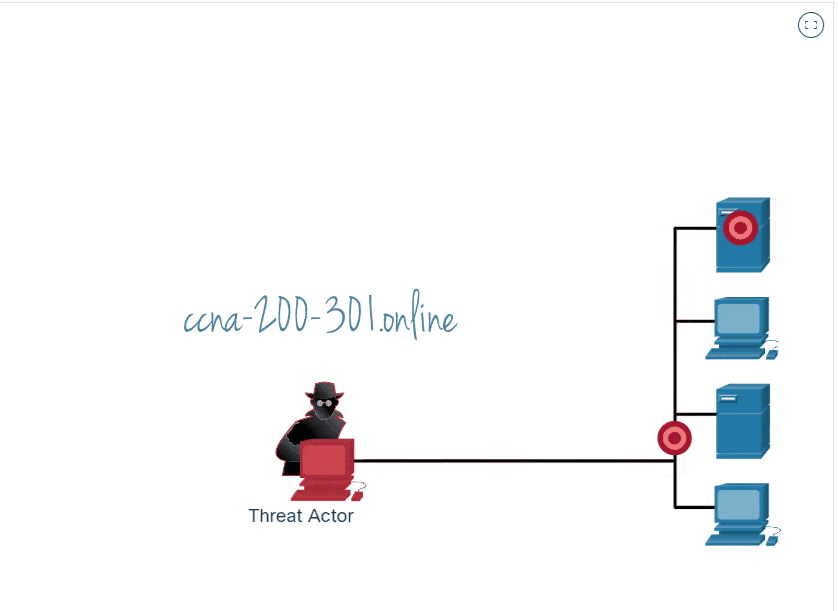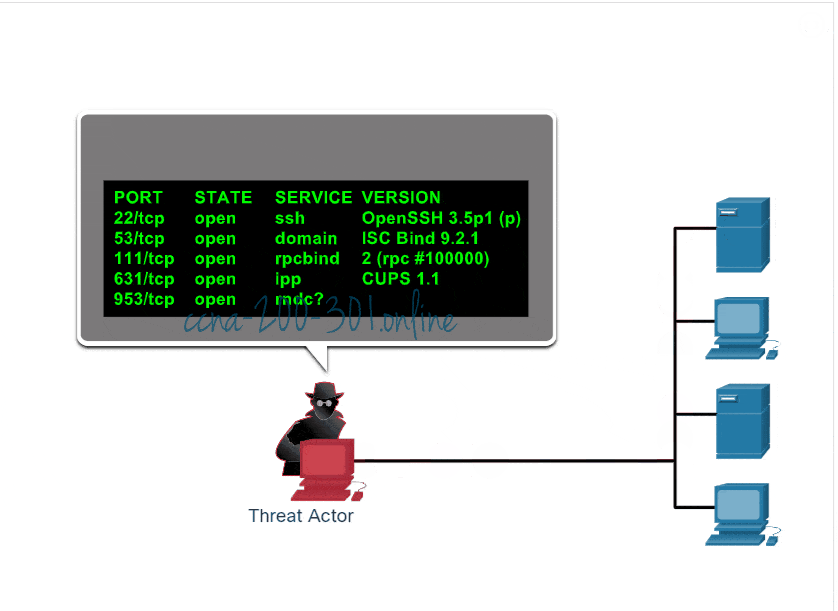
Cybersecurity port scan attacks, though unsophisticated and often harmless in and of themselves, are worth defending — and can be turned against cybercriminals. The first step in preventing malicious actors entering your network using a port scan attack is to run frequent port scans. Port scanning involves systematically scanning a computer network for open ports, which can then be exploited by threat actors to gain unauthorized access or.
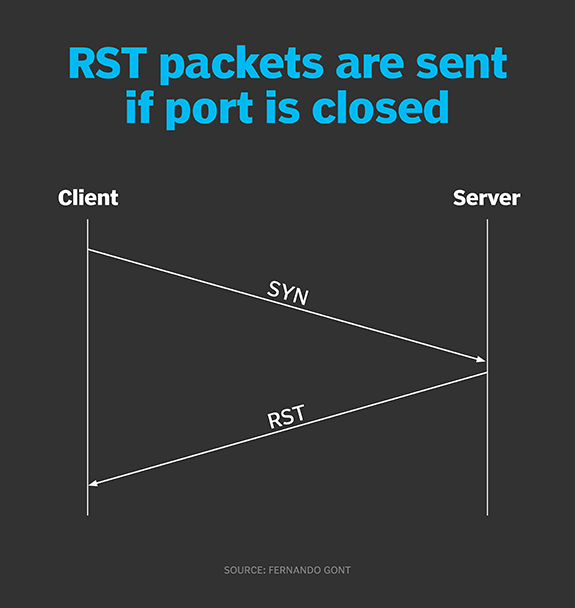
A firewall can be used to track the traffic of open ports, including both. To learn more about how to protect your network against port scanning and other attack methods, contact datto. A closed port will respond with a.
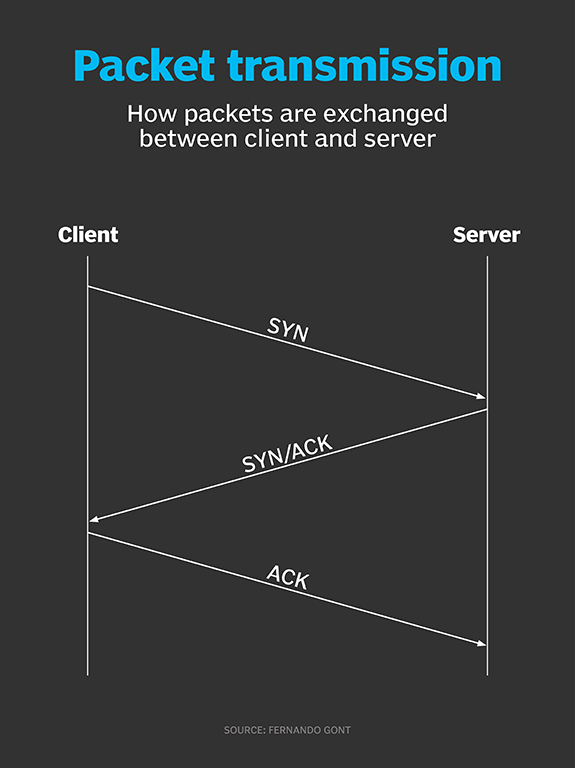
Last updated on march 3, 2023 contents: 12 portknocking portknocking is a method to open ports that the firewall normally keeps closed by executing a series of connection attempts (knocks) to other. If a port is open, or listening, it will respond to the request.
For tcp scans psad analyzes tcp. Preventing a port scan attack is reliant on having effective, updated threat intelligence that is in line with the evolving threat landscape. Learn how to identify and prevent unwanted port scans.
The preventive ways for port scan attack are listed as follows : Prevent port scan attacks with check point. Psad makes use of netfilter log messages to detect, alert, and (optionally) block port scans and other suspect traffic.
Port scanning is one of the most popular forms of. Preventing port scan attacks is normally covered if you have a comprehensive level of cloud security, as this is a very commonly used method of. Corporate firewalls can reply to a port scan in three ways:
Ask question asked 7 years ago modified 2 years, 3 months ago viewed 37k times 11 is it possible to prevent nmap from. Businesses also require strong security software, port scanning tools, and security alerts that monitor ports and prevent. Jumpfactor who consults with it & cyber security experts suggests that your first step in defending your computer against port scan attacks is to determine what.
A scanning attack is a method used by threat actors to identify vulnerabilities in a network or system. Many of the techniques used by port scanners are detectable in network traffic. Port scanning can be the start of good network security.