Beautiful Work Tips About How To Detect Dos Attack
Not sure if you're experiencing a ddos attack?
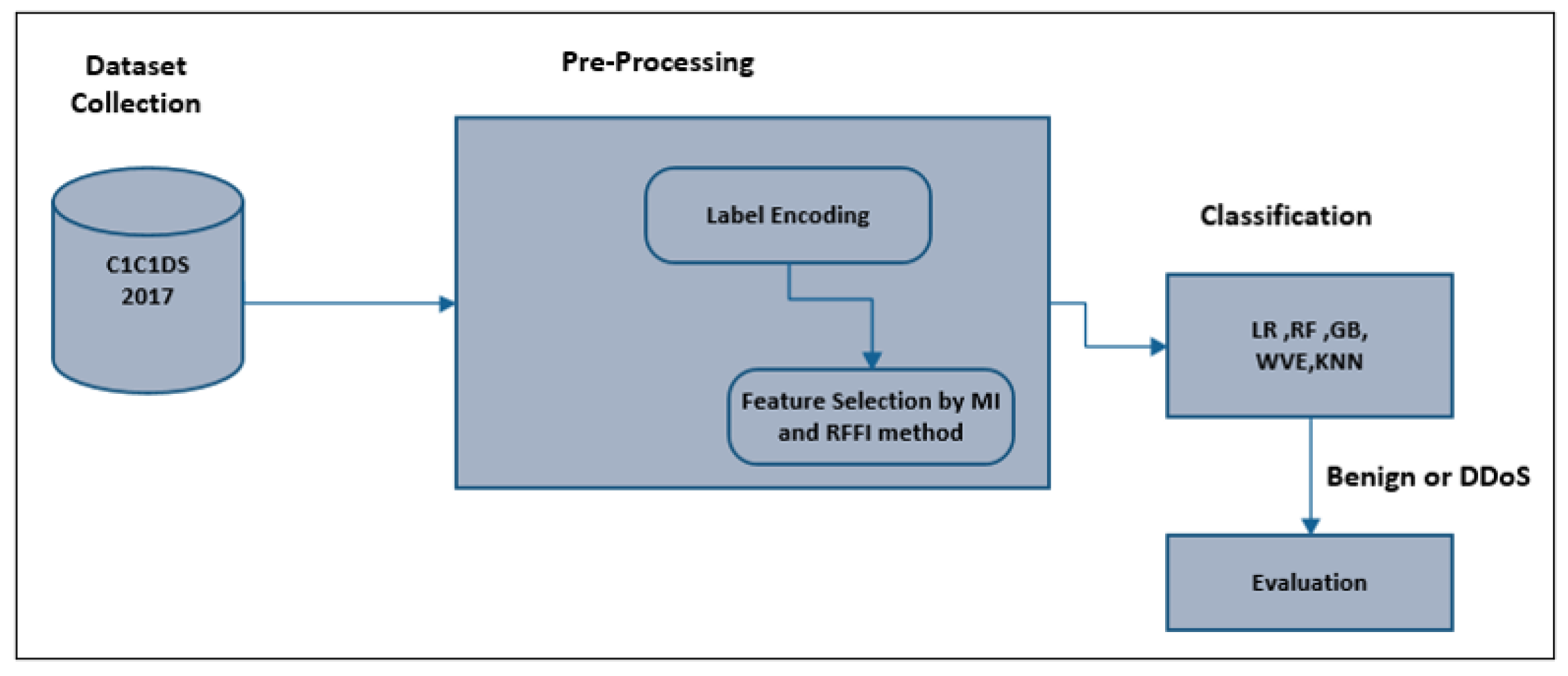
How to detect dos attack. I am looking for best practices for detecting and preventing dos in the service implementation (not external network monitoring). Learn the common signs of ddos attacks to determine if your site is under attack. Many forms of dos attacks exist, the most common types are the following:
Certain ip addresses send too many. The best way to detect and identify a dos attack would be via network traffic monitoring and analysis. Most of the models trained to detect dos and ddos.
The good news is that there will be an end to the attack. There are techniques for intrusion detection, and of course dos attack, in which for each packet (or flow) some features are calculated, then. Additionally, nausea is more commonly seen in women, heffron said, as is vomiting.
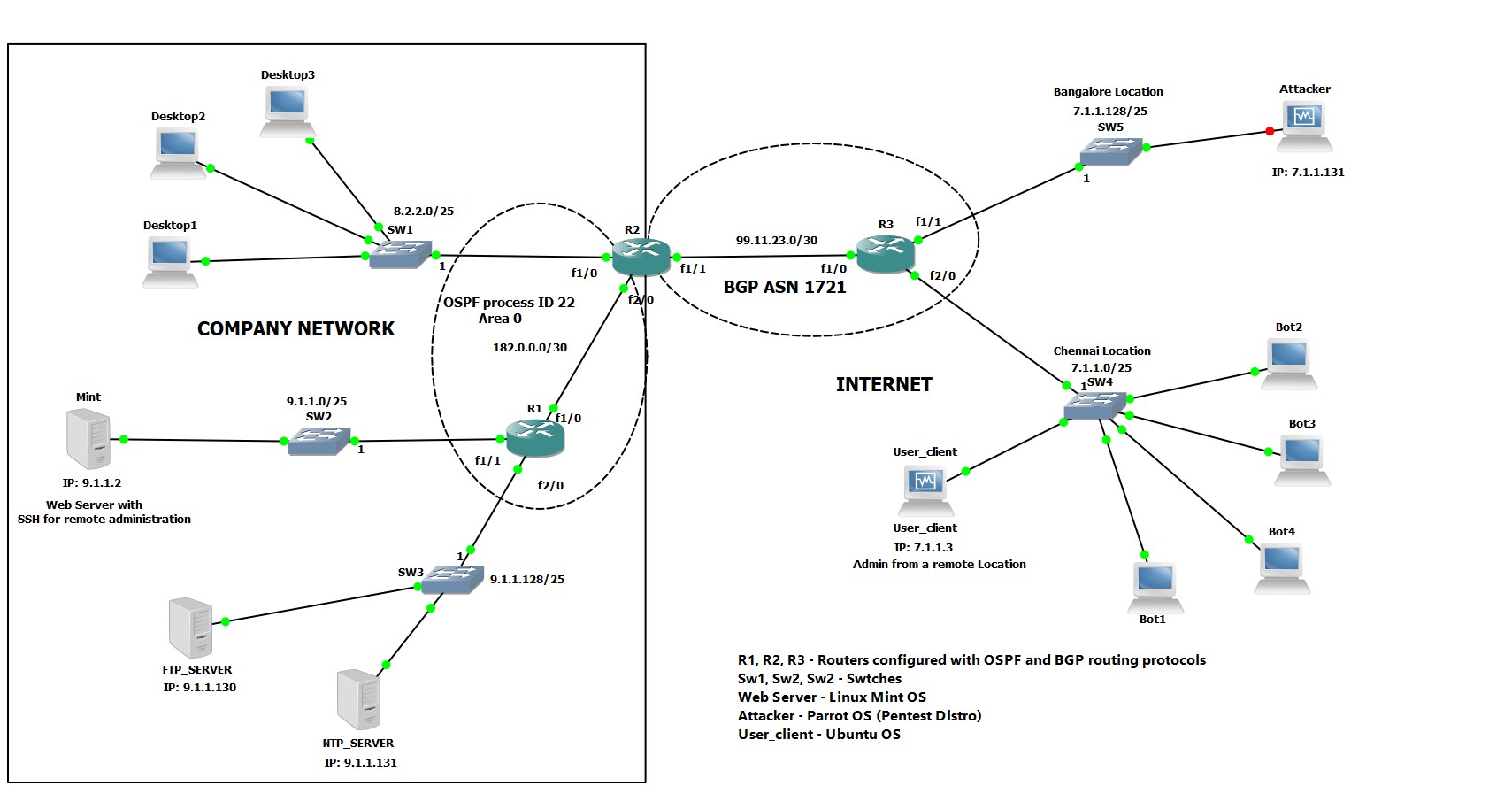
Survivors of the attack say they were hit by two himars missiles, seen here being launched in may 2023 at least 60 russian troops have been killed after a training area in. Other heart attack signs in women include jaw pain, neck pain, a dull feeling of. One common method of dos attack is the tcp syn flood, which exploits a weakness in the tcp connection establishment process to overwhelm the target with.
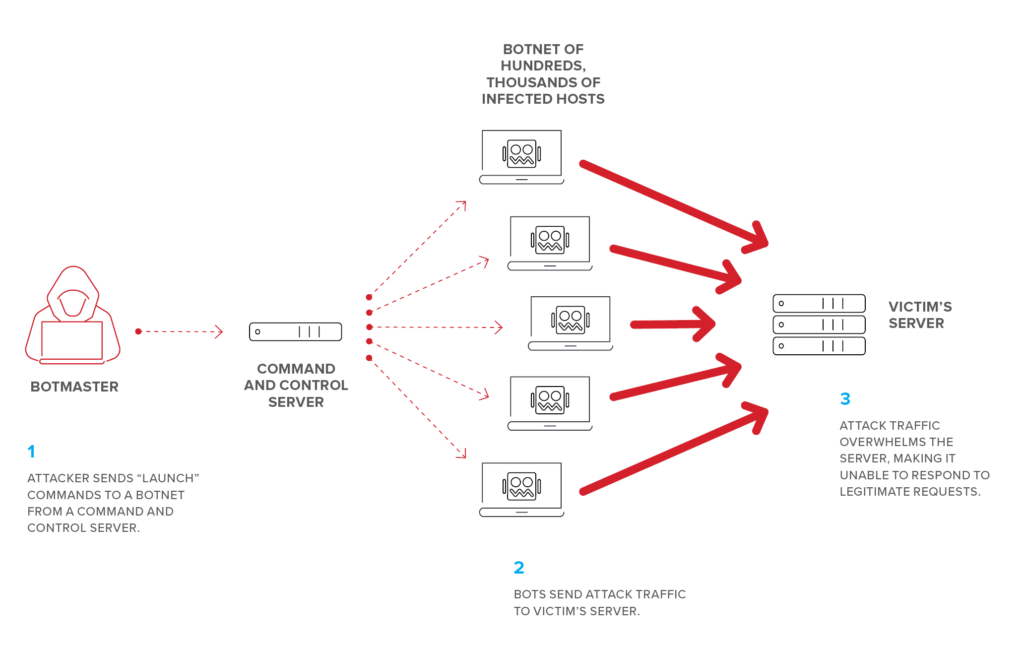
Improve this question. Dos attacks use two primary. First approach to dos attack detection:
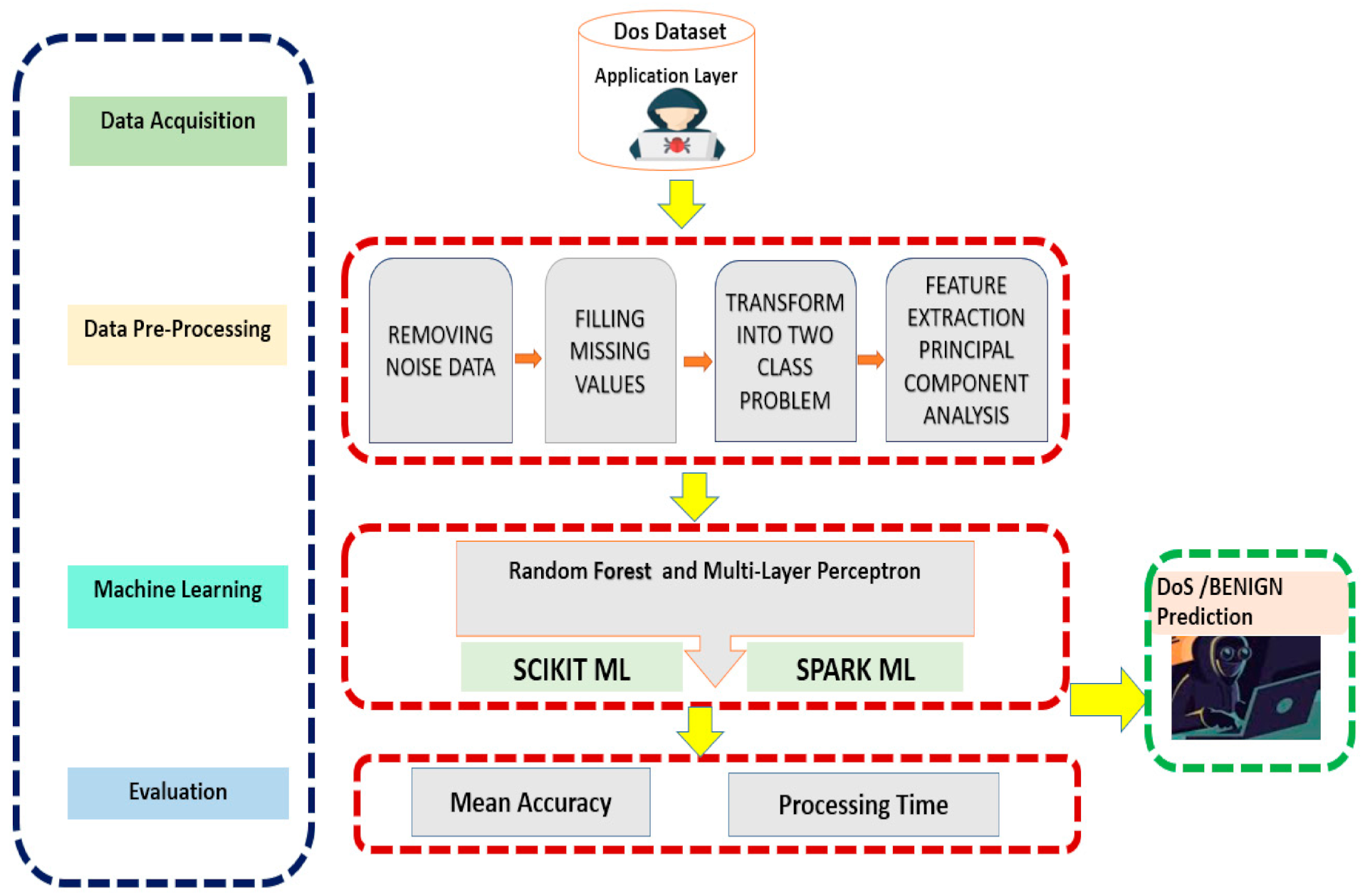
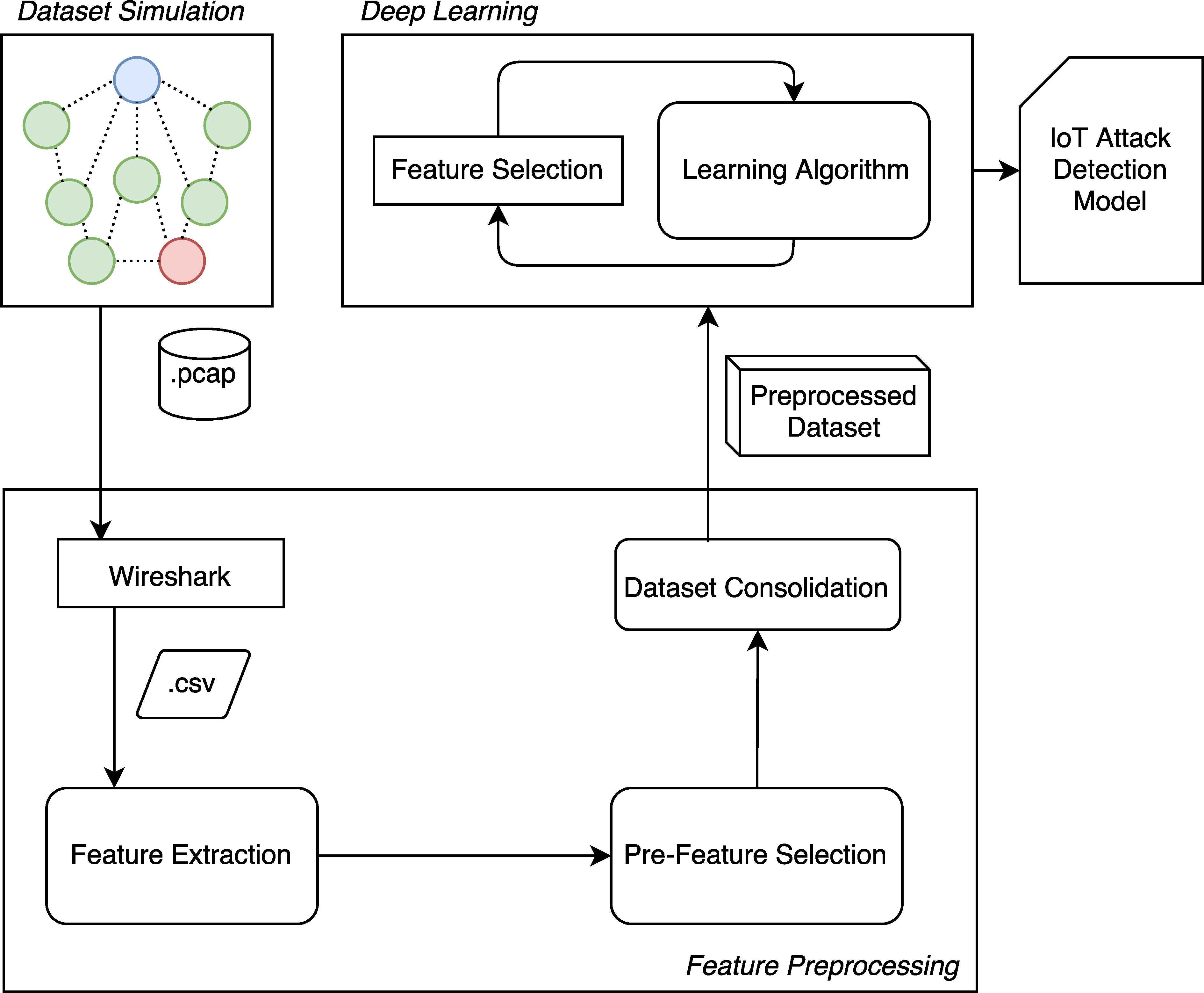
Network resource overload consumes all available network hardware, software, or bandwidth of. The main task was then to train a machine learning model to detect dos attacks and deploy it on the esp32. Once you know how a ddos attack.
Click “find anomalies” and you’ll see a screen similar to the following image: These payments are for an attack that last a specific period of time, from an hour to several hours. In this video, we explore how to detect denial of service (dos) and distributed denial of service (ddos) attacks using the powerful network analysis tool,.
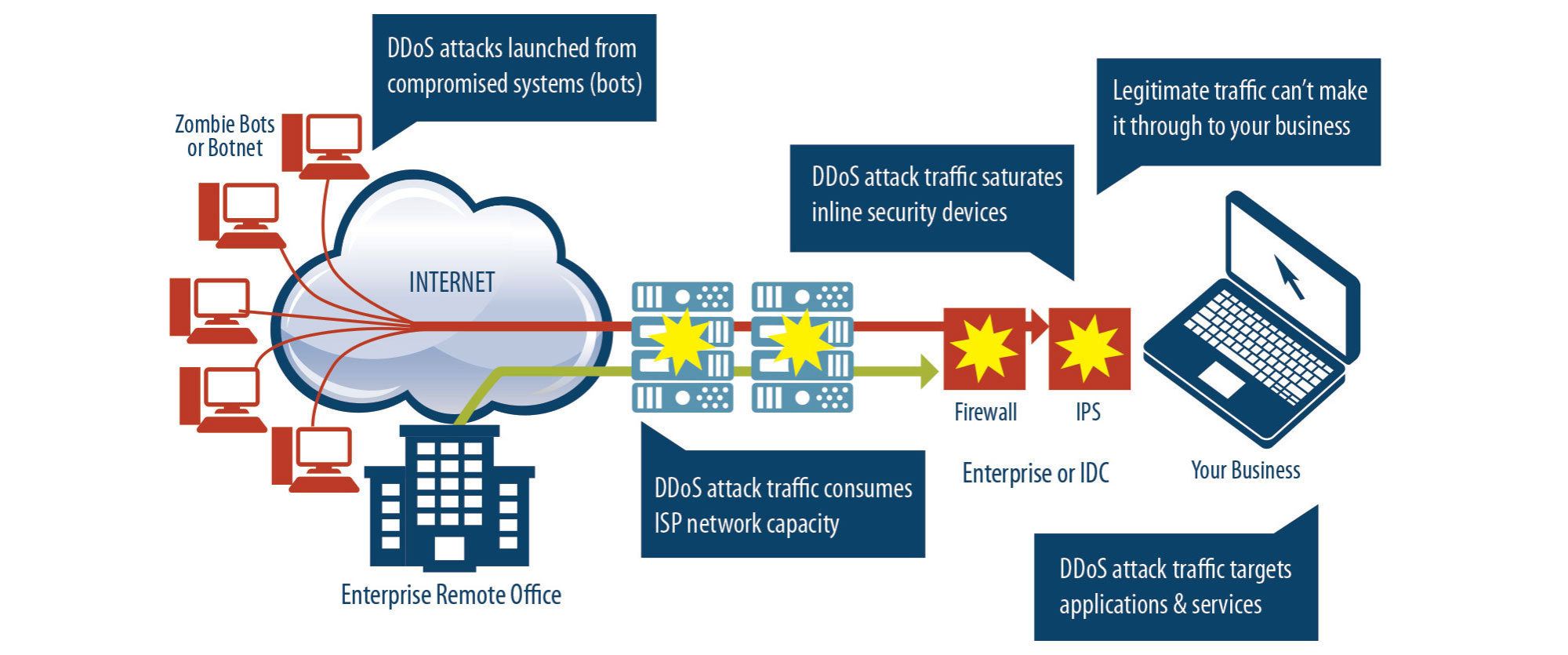
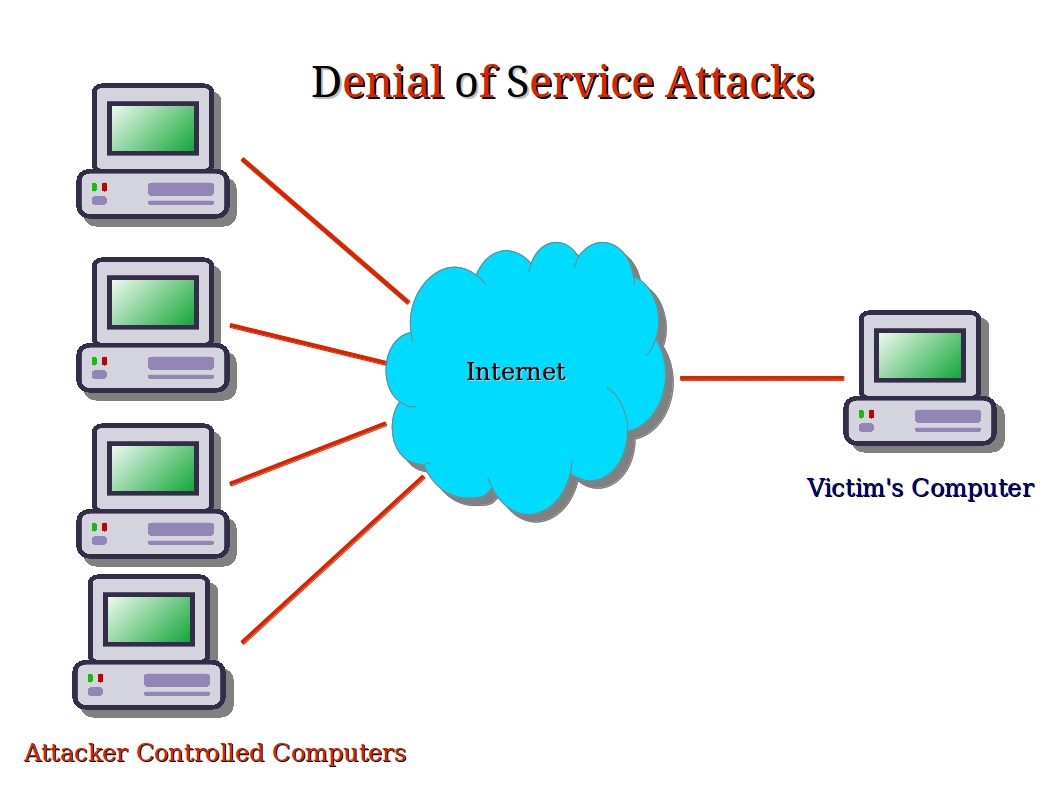
Pharmacies across the united states are experiencing disruptions following a hack at unitedhealth's technology unit, change healthcare, several pharmacy chains. Make sure you are aware of the following red flags to be able to detect a ddos attack before it takes a full swing: A dos attack involves flooding the target with an overwhelming amount of illegitimate traffic or requests, thereby consuming its available bandwidth, processing power, memory, or.
In this image, you’ll see that there is an increase in 503 status codes.